Is Captive Portal Login Safe? Understanding Risks and Security Measures
Captive portal logins are commonplace in establishments offering WiFi to guests, like hotels, cafes, restaurants, libraries, and retail stores. You might even be considering deploying them for your business. However, since it involves your wireless network, you’re probably wondering: Is captive portal login safe?
After all, you don’t want to take unnecessary security risks, especially since bad actors can exploit them. So, if you’re ready to satisfy your curiosity and find the answer to your question, let’s start!

What Is a Captive Portal?
Let’s start with a quick refresher on what a captive portal is. It is a login page to authenticate users who want to access your WiFi. For example, if you connect to a coffee shop’s network, a page will pop up on your device. It will ask you for specific information, like your order number. The page you see is a captive portal.
The above example shows how a coffee shop can limit WiFi use to paying customers. It is a way of managing user access and getting useful customer information, like email addresses and phone numbers.
How does a captive portal work? Guests who try connecting to your WiFi won’t get immediate access. Instead, their device redirects them to another page, where they need to complete the authentication process.
What your guests see on this page and what information they have to enter is up to you. For instance, you can (and should) promote your products and services on this page with your branding. Anyone who wishes to connect to your WiFi must pass through this page. To put it in another way, it can act as a marketing page.
You can ask customers to enter their names, email addresses, phone numbers, ages, and other relevant information. Not only will you keep unauthorized people at bay, but you’ll also be able to personalize your messaging.
Once customers enter their data, store it in your customer relationship management (CRM) software. The captive portal authorization process verifies the user’s credentials and grants them access to your guest network.
Understanding the Security Concerns
As you open your WiFi to the public, it’s natural to think about your captive portal security. Let’s look at what bad actors can do when you use custom WiFi splash pages in your establishment.
Overview of Common Threats
Bad actors can use your captive portal to carry out their malicious activities in several ways. Understanding what is possible gives you an idea of the risks of using these pages and how to mitigate them. The following sections highlight the various ways bad actors can cause security breaches in your network.
Man-in-the-Middle Attacks (MITM)
Bad actors often use man-in-the-middle (MITM) attacks. They use different techniques to position themselves between your network and your guests. This lets them see everything happening on your guests’ devices in real time.
For instance, cybercriminals can collect credit and debit card information if you have a payment gateway. Imagine having a private conversation with your friend over the phone. However, another person also listens to the conversation and records everything. This is how an MITM attack will take place in your wireless internet connection.
Data Interception and Phishing
Another way bad actors will hijack your network is through phishing. They may try to impersonate your business to trick your guests.
For example, they can create a WiFi network with a similar name to yours. Let’s assume your network’s name is Business_1. Bad actors can use Business__1, which, at first glance, looks the same as your WiFi. They might even set up a fake captive portal with the same branding as your business. Your guests may not even know they’re connecting to the wrong network.
They can also use malicious tools to intercept and divert the traffic in your network. For instance, your router is in an easily accessible location. The bad actors plug another device into your router for monitoring WiFi network activities.
Best Protection Practices for Users
What can your users, aka guests, do to ensure they remain safe while entering their information in your captive portal? Here are a few tips you should tell your guests to keep them safe:
- Always check the URL of the captive portal page on the browser before signing in. If it contains http, not https, they should avoid doing anything and leave the page immediately.
- Make sure to double-check the WiFi’s name before attempting to log in.
- Ensure to deactivate the auto-connect feature on any device that connects to your guest network.
- Use a VPN like Speedify, as these tools have data encryption.
- Log out of all accounts after using guest networks.
- Check for updates on all your devices because the latest firmware will fix security vulnerabilities.
What Can Businesses Do To Make These Login Pages Safer?
Businesses can make login pages safer through the following three methods:
- Implementing HTTPS and SSL Certificates
- Multi-Factor Authentication
- Leveraging DNS Filtering
Keep reading to learn how you can implement these practices when you create a captive portal.
Implementing HTTPS and SSL Certificates
The first thing you need to do is acquire a security sockets layer (SSL) for your domain. It is a file that contains identifying information about your domain. You need to host this file on your server, which enables you to use HTTPS.
This encrypts the data that goes through your domain and your users’ devices. Bad actors, even if they intercept the information, it’s almost impossible to decipher the data without the right key.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is another solution to ensure your business and your users are safe. When you enable this feature, your users must undergo another verification process.
For example, if they provide their mobile number, they’ll receive a one-time password (OTP) on their device. They must enter this code and their login credentials to access your network. Another option is to use an authenticator app, which generates time-based OTPs.
Bad actors need the login credentials and the OTP to gain access, which is highly unlikely. To put it across in another way, MFA improves your captive portal cyber security.
Leveraging DNS Filtering
Using domain name system (DNS) filtering is always a good practice. This list includes all the websites your guests can and cannot visit when using your WiFi. It’s handy to control access and prevent users from visiting certain websites that can be malicious.
For example, you can block any website known for malicious activity. Or, you can restrict access to sites that host illegal material.
Case Studies and Insights
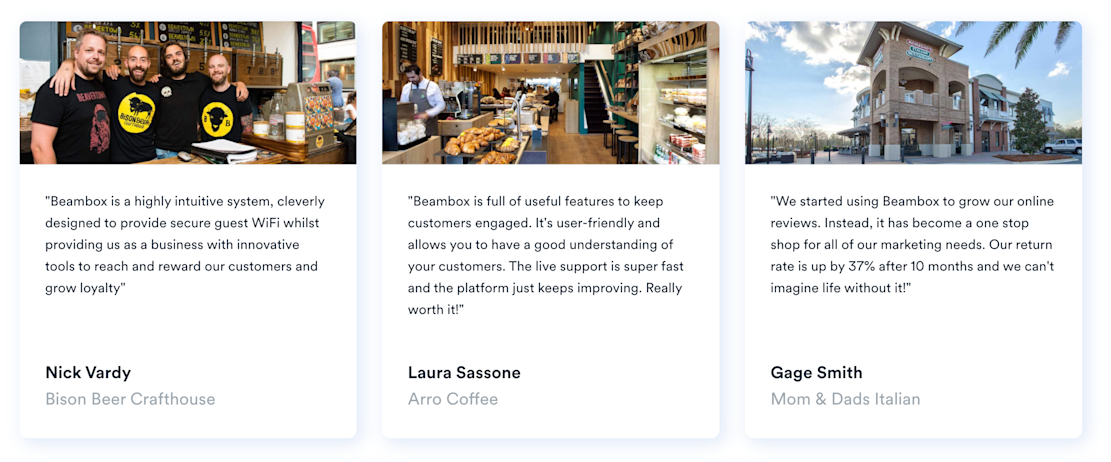
Captive portals helped countless businesses discover new and regular revenue streams. For example, Mom & Dads Italian used our captive portal solution to get more customer reviews. As a result, they noticed an increase in returning customers.
Similarly, Bison Beer Crafthouse used captive portals to easily reach their patrons. They rewarded their guests for visiting the establishment, which increased customer loyalty.
Do you also want to benefit from captive portals like these businesses? With Beambox’s WiFi marketing solution, you can provide a secure experience for guests who connect to your network. We can also automate your marketing campaigns and build your online reputation.
Start your free 30-day trial today to see how your business can benefit from captive portal solutions!
Get Started With Free WiFi Marketing
Beambox helps businesses like yours grow with data capture, marketing automation and reputation management.
Sign up for 30 days free


